- Introduction Security
- Data storage location
- Measures to protect against attacks
- Access to the platform
- Login of the back office application
- Change and reset of passwords
- The difference when logging in with HTTP-GET and HTTP-POST method
- Frequent incorrect entry of the username/password combination or PIN
- PIN
- Contact Person for Questions concerning Security
Introduction Security
In this article you will find information about the security of your data and which protection mechanisms sqanit uses. In addition, practical examples will demonstrate how you can further enhance protection in different scenarios.
| Overview Security - sqanit Private Cloud | |
|---|---|
| Certified storage location: ISO/IEC 27001:2013 | ✓ |
| Regulated by the strictest European data protection regulations | ✓ |
| Protective measures against attacks | ✓ |
| Permanent scans for vulnerabilities in software and hardware | ✓ |
| Permanent scans to detect and prevent data loss and intrusion | ✓ |
| Permanent scans for encryption vulnerabilities | ✓ |
| Permanent scans for general errors and misconfigurations | ✓ |
| Permanent scans of the API access for anomalies | ✓ |
| Regular disaster recovery tests | ✓ |
| Additional protection mechanisms optionally configurable (e.g., PIN) | ✓ |
| Secure use even for unregistered customers (e.g., code users) | ✓ |
| Role and rights management | ✓ |
For security reasons, not all details can be published here.
If you have any questions, please feel free to contact: sales@sqanit.com
Data storage location
Sqanit takes it very seriously that data is stored securely. We have therefore chosen Hetzner Online GmbH (external link) to be our partner. The Hetzner servers we use are located exclusively in the high-performance data centers in Nuremberg and Falkenstein (Germany) as well as Helsinki (Finland) and are therefore subject to the strictest European data protection regulations. Additional information on data protection and data processing can be found on the platform in the "Legal" section (link).
Measures to protect against attacks
Security measures implemented by sqanit in the background ensure that attackers are prevented from accessing data. Suspicious behavior patterns in requests are automatically recognized and blocked (e.g., brute force attacks) and the maximum request speed is limited.
Access to the platform
There are several ways to access to the digital twins and the back office application itself:
Access to digital twins as a code user
Usually, code users should be allowed to access information and documents for individual devices. For this purpose, they receive a URL that leads them to a digital twin:
- Clickable link e.g., in an email - opens URL
- QR code for scanning - opens URL
- NFC tag for scanning - opens URL
Access to the back office application with customer login
With a customer login (article), customers get access to their own back office application in addition to the digital twins. This provides further functionality, e.g., employee-, device- and ticket-overviews as well as dashboards with statistics.
Access to the back office application as an employee (main platform)
In addition to the digital twins, invited employees receive access to the back office application, which offers them further functionality, e.g., employee, device, and ticket overviews as well as dashboards with statistics. Also, depending on the permission level, employees of the main platform can change contents of the platform, enter data, edit tickets, etc.
Login of the back office application
Users (customer login or main platform) access the back office application via a login window:
- Username = Account email address
- Password = 32 digits consisting of numbers, upper and lower case letters and special characters (Base64 alphabet) (external link).
The password is initially generated randomly by sqanit, but can be changed by the user at any time.
Change and reset of passwords
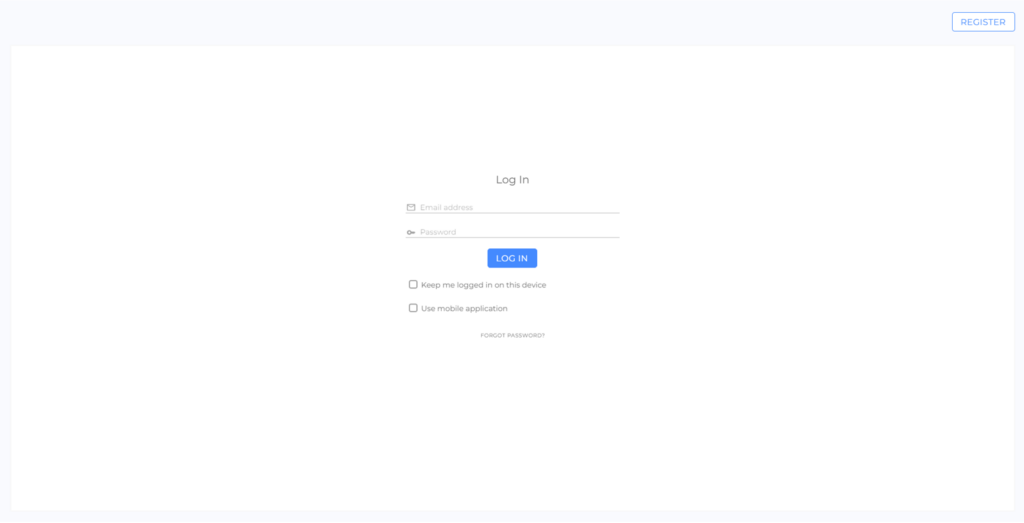
If a user forgets their login password, they can reset it at any time by clicking the "Forgot password" button in the login screen (picture).
Users can change their login passwords at any time in their profile settings (article).
Code URL parts
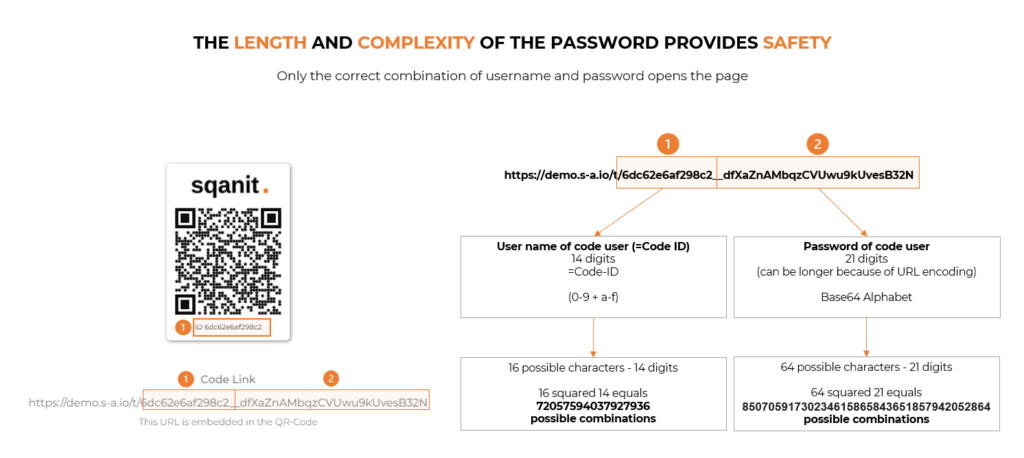
How are code URLs (links to digital twins) protected at sqanit?
Sqanit works with very long URLs for security reasons. These consist of several components (picture):
- Protocol
- Domain
- User name (code user name=code ID) and password
Username and password are generated randomly by the system and meet the highest current security standard. Compared to a man-made password, they are much more secure and almost impossible to "guess" or calculate.
With sqanit, the password part of the URL alone has 21 digits, consisting of numbers, upper and lower case letters, and special characters (Base64 alphabet) (external link). The 64 possible characters and result in 64 to the power of 21 (64^21= 85070591730234615865843651857942052864) possible combinations.
The difference when logging in with HTTP-GET and HTTP-POST method
HTTP POST method
The user's login details (username/password) are entered into a login window.
Example:
An employee uses the login window to access the back office.
HTTP GET method
The login data is delivered directly via the URL in a link.
Example:
A code user scans a QR code and the stored URL is opened. The URL contains the automatically generated username/password combination.
Note:
Whether login data is entered into a login window (username/password via HTTP-POST method) (external link) or delivered directly via the URL (via HTTP-GET method) (external link) is technically irrelevant. If you enter login data into a login window, the browser also combines it to form a URL (HTTP-POST) in the background.
Frequent incorrect entry of the username/password combination or PIN
A username/password combination that is requested too frequently via API within a short period of time will trigger the system to block access and inform administrators of the platform.
This applies to the access to codes, the login of employees, as well as the login of users of the customer login.
PIN
PINs can be used for additional protection of the code (article). To access digital twins, code users must enter a PIN.
Example QR code without PIN protection
Code users scan the code and get access to the digital twin immediately.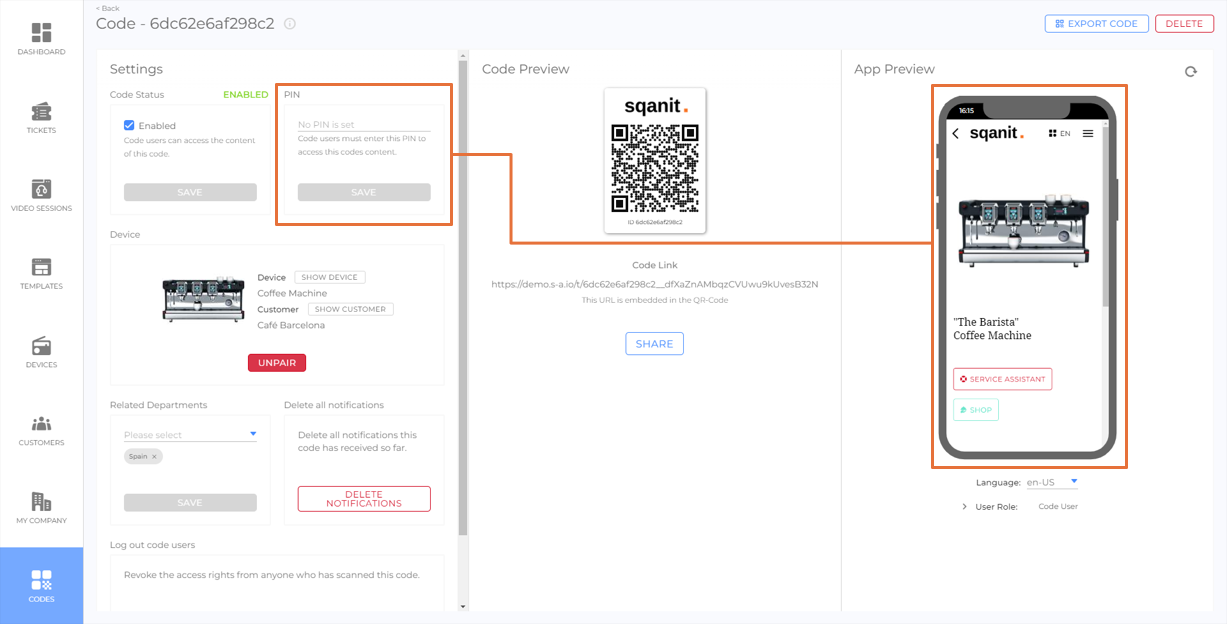
Example QR code with PIN protection
Code users scan the code and only get access to the digital twin after entering the PIN.
If a PIN is entered incorrectly five times, the code is blocked and the administrators of the platform are informed.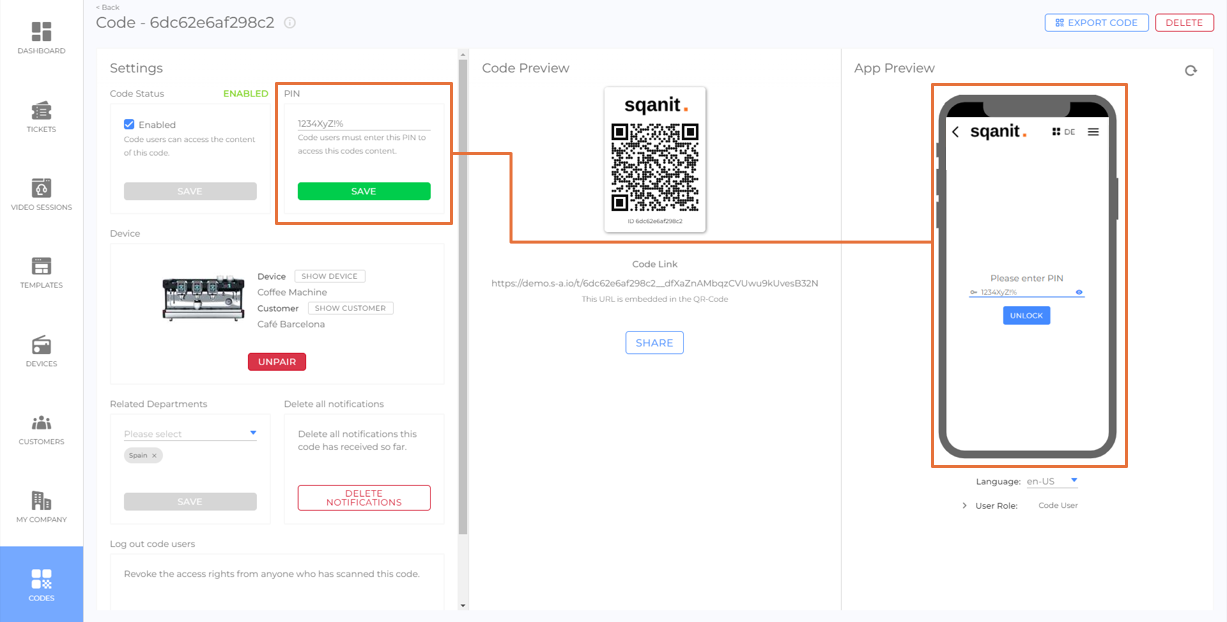
Reactivating a code after it was blocked is possible at any time by:
- logged-in employees with access rights to the device,
- logged-in employees of the customer (customer login) with access rights to the device.
Practical examples
Sqanit offers solutions for various types of business models, use cases and customer scenarios, which can be flexibly adapted. Depending on how the platform is used, there are options to further enhance data protection and limit access to certain user groups.
Example Scenario - Simple Access
Goal
The user should be able to easily look up information about the device and contact responsible persons without any barriers, such as downloading an app, creating an account, and without having to remember a password.
Suggested solution
To access the digital twins, the users receive QR code stickers (physical) and/or digital (QR codes in a PDF or URLs to click on).
Access is possible to anyone who has access to the QR code or URL. Thanks to the use of the PWA ("Progressive Web App"), it is not necessary to download an app or create an account.
Examples of how to further increase protection
- A PIN to protect the QR code
- Two codes per device: one PIN-protected code for sensitive data and one without PIN for end users in public
- Physical protection: Use existing access control of the establishment, e.g., the QR code sticker could be placed behind a service door of a device
- Create the (QR-) code only digitally, e.g., only share a link, to make it less accessible for unauthorized persons
- Use of internal tickets (chat/attachments) - only logged-in employees can see them
- Use password-protected links (e.g., IFUs to an already protected website, file hosting systems like dropbox etc.)
- Use password-protected documents (e.g., password-protected PDFs)
Maximum possible damage
Even if an unauthorized person gains access, that person only has access to a single device and thus cannot retrieve information of other devices.
Example Scenario - Access with Customer Login
Goal
A customer wants to give his employees access to all his devices on their platform.
Suggested solution
In addition to the QR code (physical and/or PDF) for the individual devices, the customer also receives a "customer login" (article).
In addition to the QR codes for individual devices, the customer is given access to the back-office application. Via this "customer login", the customer can access all his devices and the associated service cases. Each employee invited to the customer login is sent login credentials per e-mail. The username is the account email address, the password is initially chosen by sqanit, but can be changed by the user at any time.
Examples to further increase protection
- Use a PIN to protect the QR code
- Physical protection, e.g. attaching the QR code in a protected/obscure location
- Do not use QR code stickers (physical and/or PDF) - Access only via login
- Use long and secure user passwords and change them regularly
Contact Person for Questions concerning Security
If you have any further questions about this topic in your project planning, please feel free to contact: sales@sqanit.com